In the continuous battle between cyber attackers and defenders, the ultimate objective is to make software and systems autonomously cyber resilient. TNO’s Self-Healing for Cyber Security (SH4CS) software, inspired by biological defence mechanisms, offers a starting point for implementing autonomous resilience at the software deployment level.
The protection mechanisms of the human immune system against viruses, bacteria and mutations can be regarded as a sound defence-in-depth approach for the cyber security field to learn from: the body’s first line of defence (or second, if we include the human skin) is the innate immune system, which provides an immediate but non-specific response to any invader. Its goal is to disable any kind of pathogens and prevent their spread. The innate immune system is effective within minutes – it is “distributed” in the sense that it consists of cells that are present in the entire body. Aside from this defensive function, the innate immune system also “cleans” the body from foreign substances and from body cells that are at the end of their life-time. The latter function is referred to as a programmed cell death. During the “cleaning procedure” of the innate immune system, any notable presence of pathogens is signalled to the second line of defence: the adaptive immune system, which consists of cells that target specific pathogens. The weaponry for such targeted cell death is located in the Lymph nodes and thus more centralised than the innate immune system; its activation requires several tens of hours. Yet another layer of defence is the learning and memory function of the adaptive immune system. Sickness or vaccination can activate this immunization function, which can speed up the response time of the adaptive immune system at a later point in time.
This simplified description of the human body’s defensive mechanisms highlights three fundamental properties of the immune system, which we can take inspiration from to make digital systems autonomously resilient:
- Disposability: cell duplication and programmed or targeted cell death results in continuous cell regeneration, eliminating undetected abnormalities and reducing the likelihood of successful infections. Disposability of body cells is a prerequisite for the effectiveness of the immune system.
- Distribution: the more local the defence mechanism, the faster (but also less targeted) the response. The innate immune system acts much faster than the adaptive immune system, which in turn is faster than immunization.
- Response proportionality: the innate immune system is always the first line of defence. The more energy-consuming adaptive immune system is only activated to support the innate one when and where necessary.
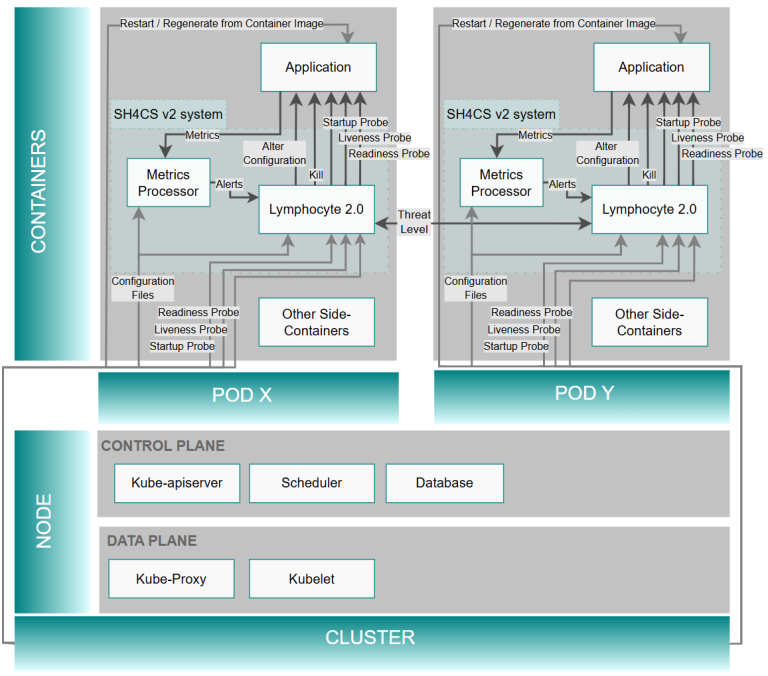
Containerisation technology combined with monitoring and deployment tools enable the incorporation of self-healing and self-protection properties into a software package to achieve (a degree of) autonomous cyber resilience. Analogous to cell death and cell regeneration in the human body, Self-Healing for Cyber Security (SH4CS) provides container regeneration that is either time-based or triggered by particular security events. From SH4CS version 2.0 onward, Kubernetes pods can also keep track of their local health level and share this information with neighbouring nodes. In TNO’s proof-of-concept implementation, a brute-force login attack combined with subsequent file downloading makes the health level of an application deteriorate to such an extent that the application is immediately restarted from a clean image. The threat notice is subsequently shared with a neighbouring test application, thus making the SH4CS concept adaptive to several types of cyber security events.
The SH4CS software primarily consists of Python code that implements (a) a decentralised rule system (referred to as the Lymphocyte software), which executes protection and healing functionality for an individual application container, and (b) a metrics processor to specify trigger events for ad-hoc container regeneration. The software was developed for modern container platforms, empowered by Kubernetes and Prometheus.
Version 2.0 of the SH4CS software features improved interaction with Kubernetes to regenerate application containers. The Lymphocyte software runs as a sidecar in the same Kubernetes POD as the application to be protected, while the metrics processor leverages the Prometheus open source software.
Version1.0 of this software was developed within the Partnership for Cyber Security Innovation (PCSI), a Dutch innovation ecosystem that features leading companies across several industries. Version 2.0 builds on feedback from PCSI partners and progressive insights, and was fully developed by TNO.